- Microsoft disclosed a vulnerability in their routinely Patch Tuesday refereced under CVE-2020-0601.
- The vulnerability was discovered by the U.S. National Security Agency in their press conference and followed by a blog post and an official security advisory.
- The flaw is located in the "CRYPT32.DLL".
-
NSA description:
-
NSA has discovered a critical vulnerability (CVE-2020-0601) affecting Microsoft Windows®1 cryptographic functionality.
-
The certificate validation vulnerability allows an attacker to undermine how Windows verifies cryptographic trust and can enable remote code execution.
-
The vulnerability affects Windows 10 and Windows Server 2016/2019 as well as applications that rely on Windows for trust functionality. Exploitation of the vulnerability allows attackers to defeat trusted network connections and deliver executable code while appearing as legitimately trusted entities.
-
Examples where validation of trust may be impacted include:
- HTTPS connections
- Signed files and emails
- Signed executable code launched as user-mode processes
-
The vulnerability places Windows endpoints at risk to a broad range of exploitation vectors.
-
NSA assesses the vulnerability to be severe and that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable.
-
The consequences of not patching the vulnerability are severe and widespread. Remote exploitation tools will likely be made quickly and widely available.
-
Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.
-
Author's note: still assessing the situation
- Microsoft Security Advisory
- NSA Security Advisory
- Microsoft BlogPost
- NSA BlogPost
- CISA-ED20-02
- CISA-Alert-aa20-014a
- CERT-FR_ALERTE
- CERT/CC VU#849224
- Matt Graeber gave a us a oneliner command to check quickly in the log if there's any evidence of an event linked to CVE-2020-0601 (Application/EID 1-2)
Get-WinEvent -FilterHashtable @{ LogName = 'Application'; Id = 1; ProviderName = 'Microsoft-Windows-Audit-CVE' } | select -Property * -ExcludeProperty MachineName, UserId
- [TBD]
- [TBD]
- [TBD]
- [TBD]
- Eg: On windows 10, the new DLL is signed with the following timestamp "Friday 3 january 2020 06:14:45"
- Eg: On Windows 10, the new DLL has the following serial number "330000023241fb59996dcc4dff000000000232"
- PowerShell & SCCM are your friends to gain a visibility in your networks
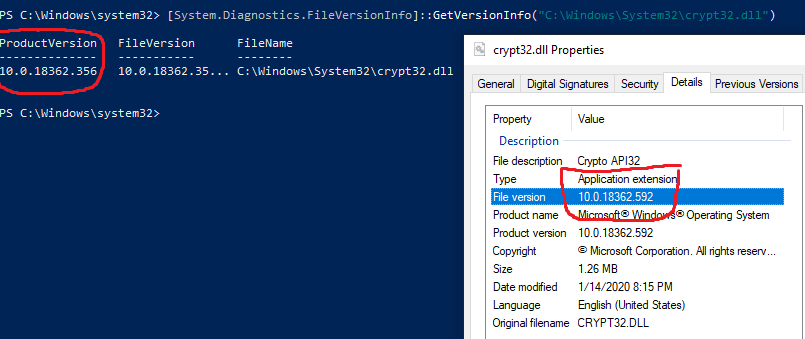



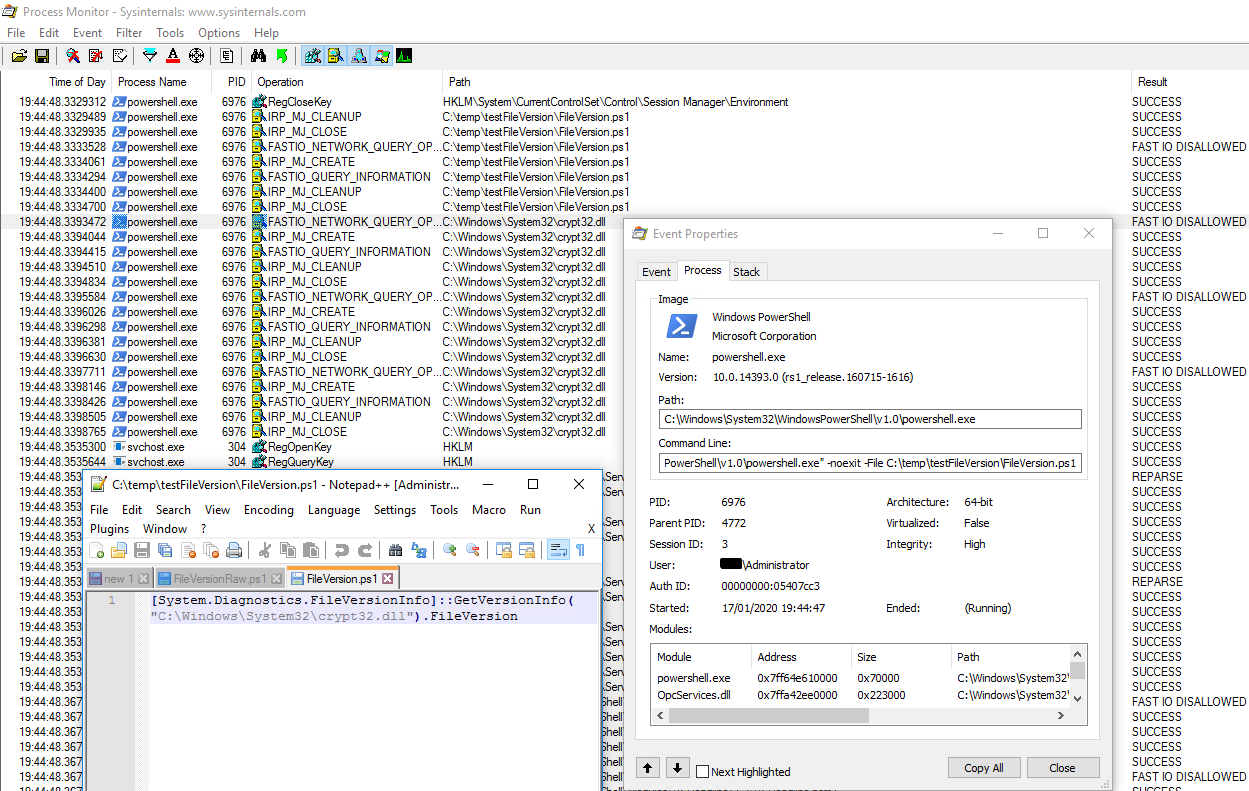

Is it possible to update only that DLL ? (I don't really want to update my entire system for 1 faulty file)
If yes, on what versions of Windows does it work ? (I have 1903 on x86 system, I can check this one for you.)