Last active
February 18, 2025 11:14
-
-
Save GAS85/42a5469b32659a0aecc60fa2d4990308 to your computer and use it in GitHub Desktop.
Revisions
-
GAS85 revised this gist
Nov 19, 2021 . 1 changed file with 6 additions and 4 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -25,10 +25,10 @@ Cipher Strength: 90% ```bash sudo a2enmod headers sudo apachectl configtest && sudo service apache2 restart ``` ### In the SSL.CONF (usually under `/etc/apache2/mods-available`) file change following lines: NOTE: _TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1._ Since using of it will avoid such clients as Windows 7 I enable both TLS 1.2. and 1.3. @@ -51,7 +51,9 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) #SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparam.pem" ``` ### In default-ssl.conf (usually under `/etc/apache2/conf-available/`). You have to provide path to your Certifcate, Pricate Key and optionally to Certificate full chain. You also need to enable `SSLEngine` and set some basic secirity headers. ```bash ServerName YOUR.Server.com @@ -66,7 +68,7 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) ### Restart Apache ```bash sudo apachectl configtest && sudo service apache2 restart ``` ### Optionally -
GAS85 revised this gist
Nov 17, 2021 . 1 changed file with 1 addition and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -18,6 +18,7 @@ Cipher Strength: 90% 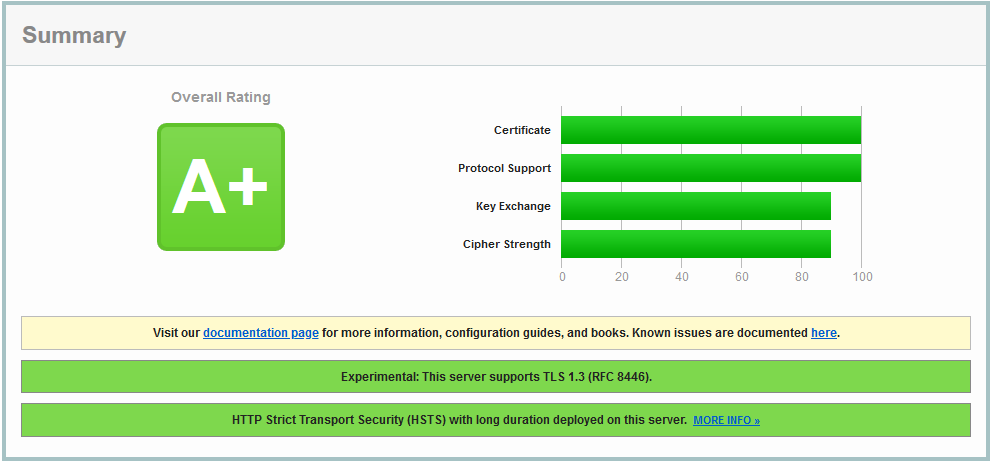 **Interesting is also** --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ **Read how to enable HTTP2.0 afterwards** --> https://gist.github.com/GAS85/990b46a3a9c2a16c0ece4e48ebce7300 ### Enable headers module and restart Apache2: -
GAS85 revised this gist
Nov 17, 2021 . 1 changed file with 26 additions and 18 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,13 +1,13 @@ ### Prerequisites * Ubuntu 20.04 (18.04, 16.04 works the same) * Apache 2.4.18 or higher * OpenSSL 1.0.2g-1ubuntu4.10 or higher * e.g. LetsEncrypt certificate ``` OS: Ubuntu 20.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 + SSL Labs: A+ RSA 2048 bits (SHA256withRSA) Certificate: 100% Protocol Support: 100% @@ -17,55 +17,63 @@ Cipher Strength: 90%  **Interesting is also** --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ **Read how to enable HTTP2.0 afterwards** --> https://gist.github.com/GAS85/990b46a3a9c2a16c0ece4e48ebce7300 ### Enable headers module and restart Apache2: ```bash sudo a2enmod headers sudo service apache2 restart ``` ### In the SSL.CONF (usually under /etc/apache2/mods-available) file change following lines: NOTE: _TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1._ Since using of it will avoid such clients as Windows 7 I enable both TLS 1.2. and 1.3. ```bash SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" # This TLSv1.3 only SSLProtocol TLSv1.3 # To use TLSv1.2 and TLSv1.3 uncomment line below and comment one above. Please read note above. #SSLProtocol +TLSv1.2 +TLSv1.3 SSLCompression off # Enable of OCSP stapling, only in httpd 2.3.3 and later SSLUseStapling on SSLStaplingResponderTimeout 5 SSLStaplingReturnResponderErrors off SSLStaplingCache shmcb:/var/run/ocsp(128000) # If you want to add DHE (Diffie-Hellman key exchange) unkomment lines below AND RUN Command from "Optional" below #SSLOpenSSLConfCmd Curves secp384r1 #SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparam.pem" ``` ### in default-ssl.conf ```bash ServerName YOUR.Server.com SSLEngine on SSLCertificateFile /etc/letsencrypt/live/YOUR.Server.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/YOUR.Server.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/YOUR.Server.com/chain.pem #Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains" Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains; preload" ``` ### Restart Apache ```bash sudo service apache2 restart ``` ### Optionally if you want to participate in Diffie-Hellman key exchange run and take a coffee: ```bash sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096 ``` after that uncomment last 2 lines in SSL.conf and restart apache2 @@ -79,7 +87,7 @@ If you would like to enable Certificate Pinning, please read here about: https:/ * valid for all, still a lot of weak Ciphers [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_1.png): SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" * still valid for all (being used in example above) [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_2.png): SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" * IE11/WinPhone 8.1 will not be able to connect as also Safari before 9 [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_3.png): -
GAS85 revised this gist
Dec 5, 2019 . 1 changed file with 2 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -69,6 +69,8 @@ if you want to participate in Diffie-Hellman key exchange run and take a coffee: after that uncomment last 2 lines in SSL.conf and restart apache2 If you would like to enable Certificate Pinning, please read here about: https://gist.github.com/GAS85/a668b941f84c621a15ff581ae968e4cb --- P.S. if you would like to reduce amount of ciphers to use to minimum of most secured, please use one of following: * valid for all, but a lot of weaks Ciphers [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_0.png): -
GAS85 revised this gist
Dec 4, 2019 . 1 changed file with 1 addition and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -63,7 +63,7 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) ```sudo service apache2 restart ``` ### Optionally if you want to participate in Diffie-Hellman key exchange run and take a coffee: sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096 -
GAS85 revised this gist
Dec 4, 2019 . 1 changed file with 2 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -15,6 +15,8 @@ Key Exchange: 90% Cipher Strength: 90% ```  ### Interesting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ### Read how to enable HTTP2.0 afterwards --> https://gist.github.com/GAS85/990b46a3a9c2a16c0ece4e48ebce7300 -
GAS85 revised this gist
Dec 4, 2019 . 1 changed file with 5 additions and 5 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -69,18 +69,18 @@ after that uncomment last 2 lines in SSL.conf and restart apache2 --- P.S. if you would like to reduce amount of ciphers to use to minimum of most secured, please use one of following: * valid for all, but a lot of weaks Ciphers [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_0.png): SSLCipherSuite HIGH:!aNULL * valid for all, still a lot of weak Ciphers [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_1.png): SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" * still valid for all [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_2.png): SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" * IE11/WinPhone 8.1 will not be able to connect as also Safari before 9 [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_3.png): SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" * *IE11 on all Windows devices*, except Windows 10 will **not** be able to connect as also old Safari [screenshot](https://raw.githubusercontent.com/GAS85/resources/master/sslCiphers_4.png): SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384" -
GAS85 revised this gist
Dec 4, 2019 . 1 changed file with 13 additions and 6 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -30,6 +30,7 @@ NOTE: _TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1._ S ``` SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" # This TLSv1.2 only SSLProtocol TLSv1.2 # To use TLSv1.2 and TLSv1.3 uncomment line below and comment one above. Please read note above. @@ -68,12 +69,18 @@ after that uncomment last 2 lines in SSL.conf and restart apache2 --- P.S. if you would like to reduce amount of ciphers to use to minimum of most secured, please use one of following: * valid for all, but a lot of weaks Ciphers 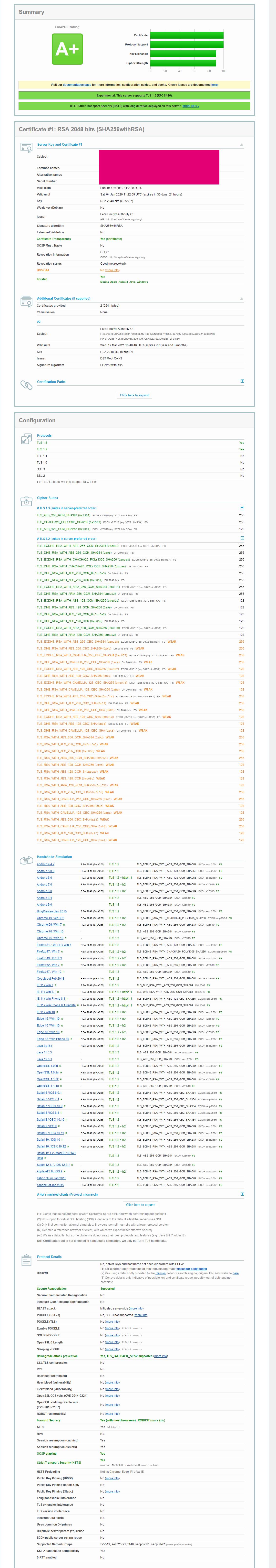: SSLCipherSuite HIGH:!aNULL * valid for all, still a lot of weak Ciphers 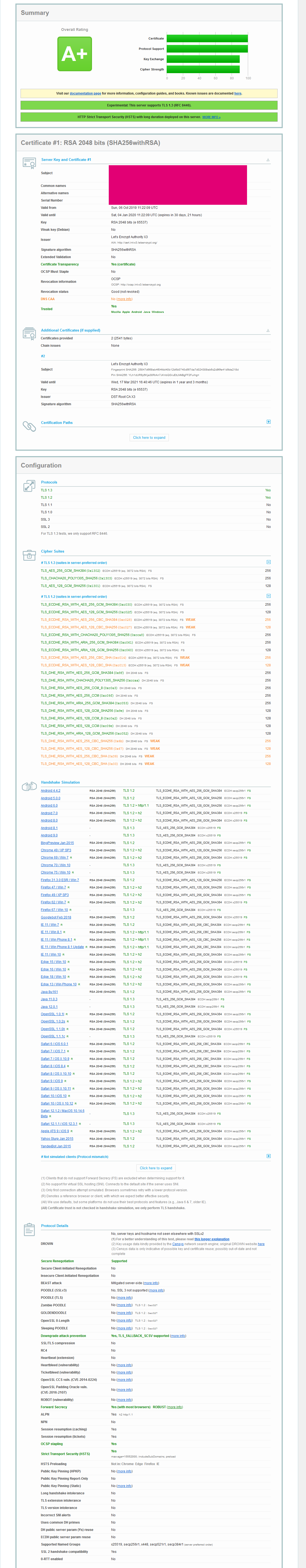: SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" * still valid for all : SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" * IE11/WinPhone 8.1 will not be able to connect as also Safari before 9 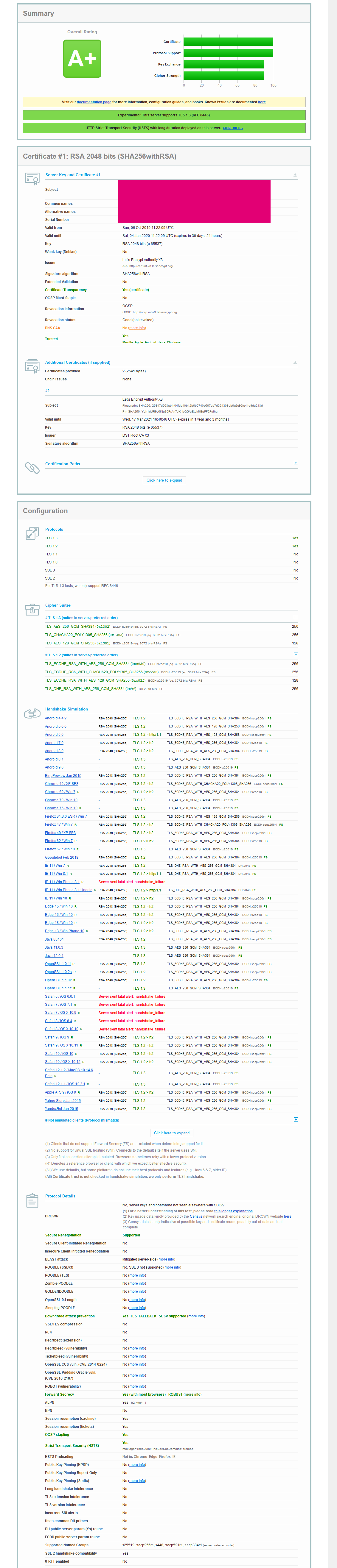: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:DHE-RSA-AES256-GCM-SHA384" * *IE11 on all Windows devices*, except Windows 10 will **not** be able to connect as also old Safari 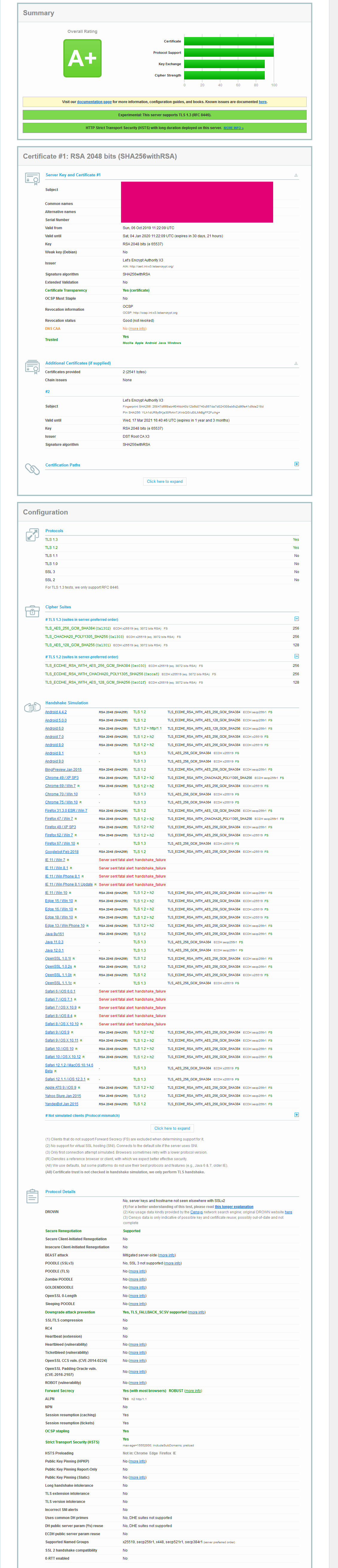: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384" -
GAS85 revised this gist
Sep 6, 2019 . 1 changed file with 2 additions and 2 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,13 +1,13 @@ ### Prerequisites * Ubuntu 18.04 (16.04 works the same) * Apache 2.4.18 or higher * OpenSSL 1.0.2g-1ubuntu4.10 or higher * e.g. LetsEncrypt certificate ``` OS: Ubuntu 18.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 SSL Labs: A+ RSA 2048 bits (SHA256withRSA) Certificate: 100% Protocol Support: 100% -
GAS85 revised this gist
Jun 19, 2019 . 1 changed file with 1 addition and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -16,6 +16,7 @@ Cipher Strength: 90% ``` ### Interesting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ### Read how to enable HTTP2.0 afterwards --> https://gist.github.com/GAS85/990b46a3a9c2a16c0ece4e48ebce7300 ### Enable headers module: ``` -
GAS85 revised this gist
Jun 12, 2019 . 1 changed file with 5 additions and 5 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,5 +1,5 @@ ### Prerequisites * Ubuntu 16.04 or higher (18.04 works the same) * Apache 2.4.18 or higher @@ -15,7 +15,7 @@ Key Exchange: 90% Cipher Strength: 90% ``` ### Interesting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ### Enable headers module: ``` @@ -58,15 +58,15 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) ### Restart Apache ```sudo service apache2 restart ``` ### Optionally if you wand to participate in Diffie-Hellman key exchange run and take a coffee: sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096 after that uncomment last 2 lines in SSL.conf and restart apache2 --- P.S. if you would like to reduce amount of ciphers to use to minimum of most secured, please use one of following: * still valid for all: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256" -
GAS85 revised this gist
Mar 1, 2019 . 1 changed file with 9 additions and 4 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -2,8 +2,8 @@ ### Prerequsits * Ubuntu 16.04 or higher (18.04 works the same) * Apache 2.4.18 or higher * OpenSSL 1.0.2g-1ubuntu4.10 or higher * e.g. LetsEncrypt certificate ``` @@ -24,10 +24,15 @@ sudo service apache2 restart ``` ### In the SSL.CONF (usually under /etc/apache2/mods-available) file change following lines: NOTE: _TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1._ Since using of it will avoid such clients as Windows 7 I enable both TLS 1.2. and 1.3. ``` SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" # This TLSv1.2 only SSLProtocol TLSv1.2 # To use TLSv1.2 and TLSv1.3 uncomment line below and comment one above. Please read note above. #SSLProtocol +TLSv1.2 +TLSv1.3 SSLCompression off #enable of OCSP stapling, only in httpd 2.3.3 and later @@ -68,6 +73,6 @@ after that uncomment last 2 lines in SSL.conf and restart apache2 * IE11/WinPhone 8.1 will not be able to connect: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384" * *IE11 on all Windows devices*, except Windows 10 will **not** be able to connect: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256" -
GAS85 revised this gist
Mar 1, 2019 . 1 changed file with 2 additions and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,7 +1,7 @@ ### Prerequsits * Ubuntu 16.04 or higher (18.04 works the same) * Apache 2.4.18 * OpenSSL 1.0.2g-1ubuntu4.10 * e.g. LetsEncrypt certificate @@ -24,6 +24,7 @@ sudo service apache2 restart ``` ### In the SSL.CONF (usually under /etc/apache2/mods-available) file change following lines: _TLSv1.3 is now supported in Apache2 version 2.4.36 with OpenSSL 1.1.1._ ``` SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" SSLProtocol TLSv1.2 -
GAS85 revised this gist
Apr 20, 2018 . 1 changed file with 3 additions and 2 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -34,7 +34,7 @@ SSLUseStapling on SSLStaplingResponderTimeout 5 SSLStaplingReturnResponderErrors off SSLStaplingCache shmcb:/var/run/ocsp(128000) #if you want to add DHE (Diffie-Hellman key exchange) unkomment lines below AND RUN Command from "Optional" below #SSLOpenSSLConfCmd Curves secp384r1 #SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparam.pem" ``` @@ -52,7 +52,8 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) ### Restart Apache ```sudo service apache2 restart ``` ### Optinally if you wand to participate in Diffie-Hellman key exchange run and take a coffe: sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096 -
GAS85 revised this gist
Apr 20, 2018 . 1 changed file with 9 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -34,6 +34,9 @@ SSLUseStapling on SSLStaplingResponderTimeout 5 SSLStaplingReturnResponderErrors off SSLStaplingCache shmcb:/var/run/ocsp(128000) #if you want to add DHE (Diffie-Hellman key exchange) unkomment lines below AND RUN Command from "Optionl" #SSLOpenSSLConfCmd Curves secp384r1 #SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparam.pem" ``` ### in default-ssl.conf @@ -49,6 +52,12 @@ SSLStaplingCache shmcb:/var/run/ocsp(128000) ### Restart Apache ```sudo service apache2 restart ``` ### Optinally if you wand to participate in Diffie-Hellman key exchange run: sudo openssl dhparam -out /etc/ssl/certs/dhparam.pem 4096 after that uncomment last 2 lines in SSL.conf and restart apache2 --- P.S. if you would liket to reduce amount of ciphers to use to minimum of most secured, please use one of follwoing: * still valid for all: -
GAS85 revised this gist
Apr 18, 2018 . 1 changed file with 22 additions and 3 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -23,12 +23,19 @@ sudo a2enmod headers sudo service apache2 restart ``` ### In the SSL.CONF (usually under /etc/apache2/mods-available) file change following lines: ``` SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" SSLProtocol TLSv1.2 SSLCompression off #enable of OCSP stapling, only in httpd 2.3.3 and later SSLUseStapling on SSLStaplingResponderTimeout 5 SSLStaplingReturnResponderErrors off SSLStaplingCache shmcb:/var/run/ocsp(128000) ``` ### in default-ssl.conf ``` ServerName YOUR.Server.com @@ -40,4 +47,16 @@ SSLCompression off Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains; preload" ``` ### Restart Apache ```sudo service apache2 restart ``` --- P.S. if you would liket to reduce amount of ciphers to use to minimum of most secured, please use one of follwoing: * still valid for all: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256" * IE11/WinPhone 8.1 will not be able to connect: SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384" * *IE11 on all devices*, except Windows 10 will not be able to connect SSLCipherSUite "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256" -
GAS85 revised this gist
Apr 18, 2018 . 1 changed file with 1 addition and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -4,6 +4,7 @@ * Ubuntu 16.04 * Apache 2.4.18 * OpenSSL 1.0.2g-1ubuntu4.10 * e.g. LetsEncrypt certificate ``` OS: Ubuntu 16.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 -
GAS85 revised this gist
Apr 18, 2018 . 1 changed file with 8 additions and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,3 +1,10 @@ ### Prerequsits * Ubuntu 16.04 * Apache 2.4.18 * OpenSSL 1.0.2g-1ubuntu4.10 ``` OS: Ubuntu 16.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 SSL Labs: A+ RSA 2048 bits (SHA256withRSA) @@ -9,7 +16,7 @@ Cipher Strength: 90% ### Intresting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ### Enable headers module: ``` sudo a2enmod headers sudo service apache2 restart -
GAS85 revised this gist
Apr 4, 2018 . 1 changed file with 11 additions and 5 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,29 +1,35 @@ ``` OS: Ubuntu 16.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 SSL Labs: A+ RSA 2048 bits (SHA256withRSA) Certificate: 100% Protocol Support: 100% Key Exchange: 90% Cipher Strength: 90% ``` ### Intresting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ###Enable headers module: ``` sudo a2enmod headers sudo service apache2 restart ``` ### In the SSL.CONF file change following lines: ``` SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" SSLProtocol TLSv1.2 SSLCompression off ``` ### in default-ssl.conf ``` ServerName YOUR.Server.com SSLEngine on SSLCertificateFile /etc/letsencrypt/live/YOUR.Server.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/YOUR.Server.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/YOUR.Server.com/chain.pem #Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains" Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains; preload" ``` ### Restart Apache ```sudo service apache2 restart ``` -
GAS85 renamed this gist
Apr 4, 2018 . 1 changed file with 0 additions and 0 deletions.There are no files selected for viewing
File renamed without changes. -
GAS85 renamed this gist
Apr 4, 2018 . 1 changed file with 0 additions and 0 deletions.There are no files selected for viewing
File renamed without changes. -
GAS85 created this gist
Jan 26, 2018 .There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -0,0 +1,29 @@ OS: Ubuntu 16.04 Apache/2.4.18 1.0.2g-1ubuntu4.10 SSL Labs: A+ RSA 2048 bits (SHA256withRSA) Certificate: 100% Protocol Support: 100% Key Exchange: 90% Cipher Strength: 90% # intresting is also --> https://mozilla.github.io/server-side-tls/ssl-config-generator/ ###Enable headers module: sudo a2enmod headers sudo service apache2 restart ### In the SSL.CONF file change following lines: SSLCipherSUite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH EDH+aRSA !CAMELLIA !SEED !3DES !RC4 !aNULL !eNULL !LOW !MD5 !EXP !PSK !SRP !DSS" SSLProtocol TLSv1.2 SSLCompression off ### in default-ssl.conf ServerName YOUR.Server.com SSLEngine on SSLCertificateFile /etc/letsencrypt/live/YOUR.Server.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/YOUR.Server.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/YOUR.Server.com/chain.pem #Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains" Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains; preload" ### Restart Apache sudo service apache2 restart