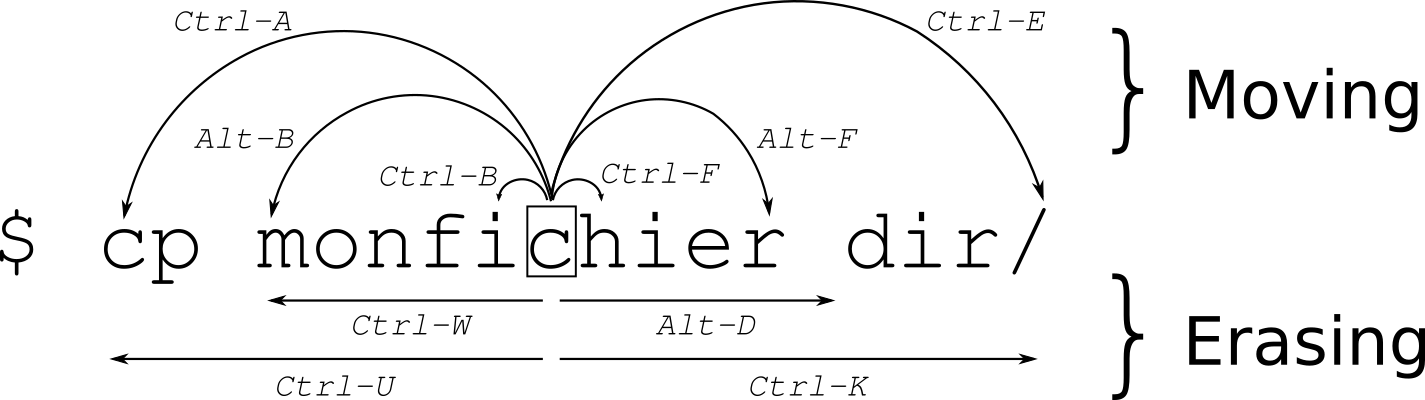
| command | description |
|---|---|
| ctrl + a | Goto BEGINNING of command line |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| # .htaccess Security Protection Guide | |
| [](https://github.com/yourusername/htaccess-security-guide) | |
| [](LICENSE) | |
| [](README_TH.md) | |
| ## 📋 Table of Contents | |
| - [Overview](#overview) | |
| - [Common Attack Vectors](#common-attack-vectors) |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/usr/bin/env bash | |
| # Allows you to connect to remote endpoints via port forward | |
| set -e | |
| TEMP_POD_NAME=db-jump-server | |
| LOCAL_PORT=3307 | |
| REMOTE_HOST=prod.abc123.region-1.rds.amazonaws.com | |
| REMOTE_PORT=3306 | |
| function cleanup { |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #curl 127.0.0.1:8001/services -d name=1 -d url=http://httpbin.org/status/201 | |
| #curl 127.0.0.1:8001/services/1/routes -d name=a -d paths[]=/a | |
| #curl 127.0.0.1:8001/services -d name=2 -d url=http://httpbin.org/status/202 | |
| #curl 127.0.0.1:8001/services/2/routes -d name=b -d paths[]=/b | |
| #curl 127.0.0.1:8001/services/1/plugins \ | |
| -d name=oauth2 -d config.mandatory_scope=false \ | |
| -d config.global_credentials=true \ | |
| -d config.enable_client_credentials=true |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| version: '3.9' | |
| services: | |
| restart-docker: | |
| image: jpetazzo/dind | |
| restart: always | |
| volumes: | |
| - /var/run/docker.sock:/var/run/docker.sock | |
| command: sh -c "docker start $(docker ps -aq) && tail -f /dev/null || exit 0;" | |
| logging: |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| host=127.0.0.1 | |
| port=8001 | |
| #for object in services routes plugins consumers certificates upstreams snis tags;do | |
| for object in services routes certificates upstreams snis ;do | |
| # cout=$(curl -sL $host:$port/$object | jq .data | jq .[] | jq .id | wc -l) | |
| for i in $(curl -sL $host:8001/$object | jq .data | jq .[] | jq .name); do | |
| j=$(echo $i | sed 's,",,g'); |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| host=127.0.0.1 | |
| port=8001 | |
| for object in services routes plugins consumers certificates upstreams snis tags;do | |
| cout=$(curl -sL $host:$port/$object | jq .data | jq .[] | jq .id | wc -l) | |
| offset=$(curl -sL $host:$port/$object | grep -o '"offset":"[^"]*' | grep -o '[^"]*$'); | |
| while [ "$offset" != "" ];do | |
| cout=$(($cout + $(curl -sL $host:$port/$object?offset=$offset | jq .data | jq .[] | jq .id | wc -l))) |
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #datainhost=$(du -hsb /data/do-3/root | awk '{print $1}') | |
| #echo $datainhost | |
| #x=1 | |
| #while [ $datainhost -lt 115598085 ] | |
| while [ $(pidof scp) ] | |
| do | |
| #datainhost=$(du -hsb /data/do-3/root | awk '{print $1}') | |
| echo "root "$(pidof scp)" not finish" | |
| sleep 60s |
NOTE: If you have Windows 11 there is now an official way to do this in WSL 2, use it if possible - see MS post here (WINDOWS 11 ONLY)
This guide will enable systemd to run as normal under WSL 2. This will enable services like microk8s, docker and many more to just work during a WSL session. Note: this was tested on Windows 10 Build 2004, running Ubuntu 20.04 LTS in WSL 2.
-
To enable
systemdunder WSL we require a tool calledsystemd-genie -
Copy the contents of
install-sg.shto a new file/tmp/install-sg.sh:
NewerOlder