Last active
June 27, 2025 15:15
-
-
Save ceres-c/653a357a12e4c45fec44ee953056ea9a to your computer and use it in GitHub Desktop.
Revisions
-
ceres-c revised this gist
Feb 18, 2021 . 1 changed file with 5 additions and 5 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,7 +1,7 @@ # Disabling WPAD WPAD is the Windows Proxy Auto Discovery service, used since Windows 95, IIRC, to automatically discover network configurations. Since Windows 10 Microsoft decided for some reason that users shall NOT be allowed to disable this (mostly) useless and problematic service. 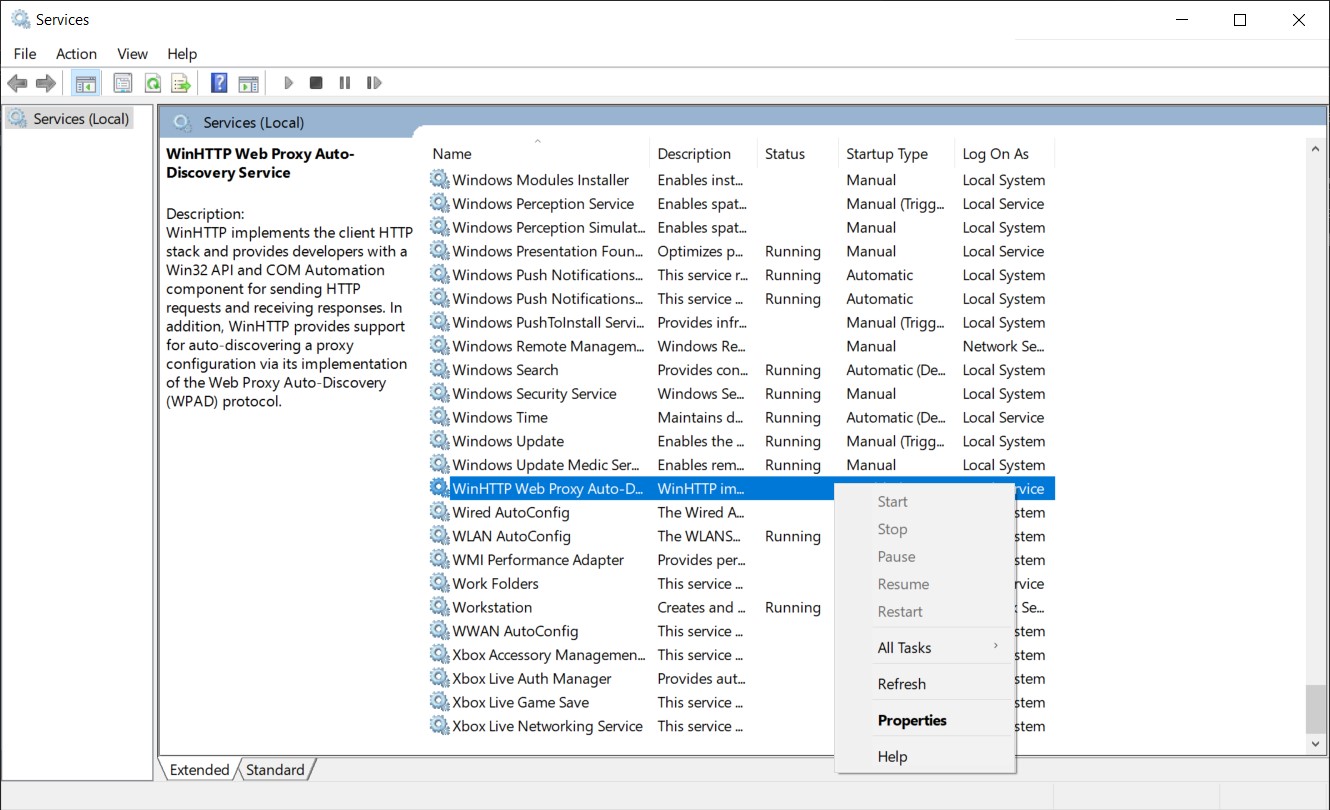 Problem is: on my laptop this _feature_ used up to 20% of the CPU while doing nothing at all due to some bug I don't want to dig into. The best part is that it often triggered **after** disconnection from a wireless network. Discovering proxies makes lot of sense once you are NOT connected to any network, huh? Also, there were multiple vulnerabilities related to this service and cute tools such as [Responder](https://github.com/SpiderLabs/Responder) leverage on it. @@ -29,18 +29,18 @@ Stop-Transcript ### The scheduled task * Create a new task, configure the General tab as follows  > **NOTE**: I configured the script to be run as SYSTEM. This is terribly UNSAFE because a world writable script will be executed with the maximum privileges. I don't care, but you might * In the Triggers tab add a new trigger on logon  * Add a new action with the following config - Action: Start a program - Program/script: `%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe` - Add argument `-NoProfile -NoLogo -NonInteractive -ExecutionPolicy Bypass -File "<POWERSHELL_SCRIPT_PATH_HERE>"` * Set the following Conditions  * Configure the Settings  Done. -
ceres-c created this gist
Feb 18, 2021 .There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -0,0 +1,47 @@ # Disabling WPAD WPAD is the Windows Proxy Auto Discovery service, used since Windows 95, IIRC, to automatically discover network configurations. Since Windows 10 Microsoft decided for some reason that users shall NOT be allowed to disable this (mostly) useless and problematic service.  Problem is: on my laptop this _feature_ used up to 20% of the CPU while doing nothing at all due to some bug I don't want to dig into. The best part is that it often triggered **after** disconnection from a wireless network. Discovering proxies makes lot of sense once you are NOT connected to any network, huh? Also, there were multiple vulnerabilities related to this service and cute tools such as [Responder](https://github.com/SpiderLabs/Responder) leverage on it. ## Killing WPAD The service can still be disabled writing in the registry, but it will be randomly re-enabled by windows after updates/who-knows-what, so the best way to prevent this is a scheduled task running on every boot which runs a powershell script to kill the service and disable it. ### The script I saved it as `wapd_kill.ps1` in my Documents folder ``` $WPADName = "WinHttpAutoProxySvc" Start-Transcript -Path Join-Path -Path $pwd -ChildPath "wapd_kill.log" Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\WinHttpAutoProxySvc -Name Start -Value 0x00000004 Write-Host "Wrote registry to disable WPAD" $WPADServ = Get-Service -Name $WPADName if ($WPADServ.Status -eq "Running") { Write-Host "WPAD is running: Stopping it" $ServicePID = (get-wmiobject win32_service | where { $_.name -eq $WPADName}).processID Stop-Process $ServicePID -Force } else { Write-Host "WPAD not found running" } Stop-Transcript ``` ### The scheduled task * Create a new task, configure the General tab as follows  > **NOTE**: I configured the script to be run as SYSTEM. This is terribly UNSAFE because a world writable script will be executed with the maximum privileges. I don't care, but you might * In the Triggers tab add a new trigger on logon  * Add a new action with the following config - Action: Start a program - Program/script: `%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe` - Add argument `-NoProfile -NoLogo -NonInteractive -ExecutionPolicy Bypass -File "<POWERSHELL_SCRIPT_PATH_HERE>"` * Set the following Conditions  * Configure the Settings  Done. Please read the above **NOTE** about security concers. This is mostly a reminder for myself, I don't advise you to follow this script, but if you're fed up with WPAD as well, this works.